Cisco Ssl Vpn Port Forwarder Activex Download
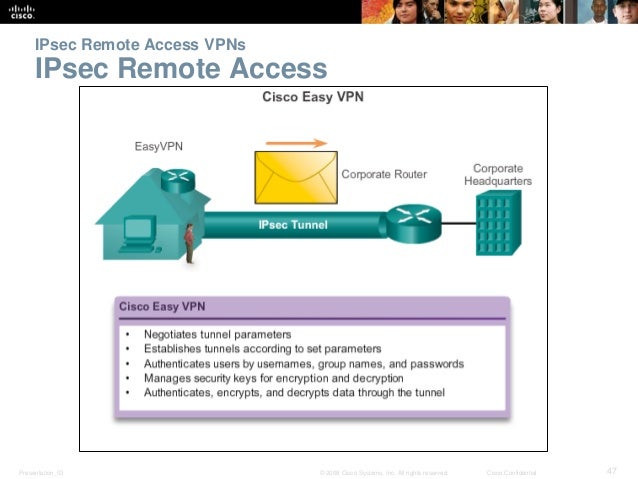
This advisory addresses the vulnerability in the Cisco Port Forwarder ActiveX control provided by Cisco ASA when the Cisco Clientless VPN feature is used. This issue is documented in Cisco bug ID CSCtr00165 (registered customers only) and has been assigned Common Vulnerabilities and Exposures (CVE) ID CVE-2012-0358. Thin-Client SSL VPN (Port Forwarding)—Provides a remote client that downloads a small Java-based applet and allows secure access for Transmission Control Protocol (TCP) applications that use static port numbers. Post Office Protocol (POP3), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), secure shell (ssh),.
We're going to be leaving our PIX 515 and going with the ASA 5510 with the SSL/VPN feature. From what I'm reading from the admin/install guides, it says the feature is entirely clientless. Anyone know if this is true? No activeX to install, no extra java stuff, entirely clientless. How's it's speed? Our home users will be using this feature to access our internal Terminal Servers.
From what I can tell, all they (the external clients) need is a trusted certificate. Just looking for advice or opinions from anyone who's used this feature. RE: Anyone using the SSL/VPN features? The SSL Features on the ASA are pretty great. I have configured it a bunch of times, though I'll admit I didn't necessarily run it in production, so I can't promise perfection. Russkie runi tatischev tv.
The SSL solution doesn't have to be clientless. If you upgrade to ASA 8.0 (a must!) then you can use the full-client AnyConnect Client that installs via ActiveX or Java. AnyConnect gives your users a full-tunnel experience like the traditional IPSec client. In ASA 8.0, if you're after terminal services, you can even get by with just a clientless setup. You can install a java remote desktop plugin on the ASA that allows your users to launch a remote desktop session by clicking on a link once they login to webvpn. I've used this and it works well. In the clientless setup, the only certificate you might want to get is on the ASA itself.
While the ASA can generate its own self-signed SSL Certificate, your users' browsers will not trust it unless you install that cert on their PCs. If you buy an SSL cert from Verisign or GoDaddy, your users' browsers will trust the ASA right away because they have those roots already installed. In the AnyConnect setup, you can use normal client certificates if you want, but they are not required.
Here's a link to Cisco's SSL Config Examples: This one specifically deals with the RDP plugin: This one deals with the SSL certs I described: Matt CCSP RE: Anyone using the SSL/VPN features? Excellent info.thanks! So, the AnyConnect client, it isn't entirely clientless then beings they still have to install an activex or java plugin. That's ok I guess, but if one of our users are at a library or something with a public PC, it may not work since they probably couldn't install a plugin. And, with the ASA, if they don't have the self signed cert installed on their machines, there's no way to connect? It won't allow them to accept the certificate on a temporary basis and continue? I'll be sure to get the 8.x version, which it might even come with by now.
For terminal services, this 'java remote desktop plugin' you refer to. Is that a Cisco piece of software? RE: Anyone using the SSL/VPN features? I'm pretty sure you need administrator rights to install the AnyConnect client, so in a Library setting, you might have to go clientless.
Sorry, I wasn't clear on the certs. If the user's PC does not have the ASA's self-signed cert in its store, the user will get a popup alerting them that the certificate is valid, but not necessarily trusted. They will be able to click OK and connect with no problem, like you indicate.